Synopsis: to demonstrate the need for a holistic security
approach by utilizing publicly available tools and social engineering techniques to gain unauthorized access to systems, data, and network resources.
I'll create different scenarios in which various tools will be used for hacking purposes, after the target computer is successfully compromise I'll go over different security measures that could have been implemented to stop or mitigate the likelihood of a security breach.
Some tools and scenarios will be more technical than others but as security professional our job is not to defeat tools but to protect the resources even from unsophisticated events such as someone stealing the physical computer.
Some tools and scenarios will be more technical than others but as security professional our job is not to defeat tools but to protect the resources even from unsophisticated events such as someone stealing the physical computer.
As a side note, some of the Scenarios are real cases in the business world. Sophisticated or not they could have been avoided with the right security security measures. Any identifiable information has been modified to protect the privacy of those affected.
Too 1. Trinity Rescue Kit (TRK)
1 I came across TRK a couple of years ago and I
must confess, it’s a solid, simple to use, and intuitive tool that comes handy for the everyday tech support but i noticed that almost anyone with a little bit of imagination and basic technical skills can induce some damage to an organizations.
You can go to www.trinityhome.org to learn more about project, if you think
it’s useful and end up taking advantage of it consider making a donation, they
do a pretty good job keeping it relevant. One more thing, TRK is based on linux OS, even though it support a huge hardware variety you might encounter that some hardware is not compatible with it.
d
fScenario 1. Resetting a Password. Bob wants administrative access to Alice's PC.
Difficulty 1-10: 3
Technical skills needed: 3
The following must be met:
Physical access to the target PC
Boot up from an external source such a USB, CD, or network.
Windows Desktop Environment XP-7
Workgroup Environment
So here we go...!
Bob's is unhappy in his current job. He's putting over 60 hours a week in the office, about 17 more hours a week working remotely, he's on salary, hasn't seen a decent salary raise in the last 3 years and to top it off Alice received a promotion he was working so hard for.
Before he leaves the company he wants to access data stored on Alices' computer and take a client lists, new product documents, and inventory spreadsheets.
- Step 1. Bob gains access to Alices' physical computer. How did he do it? it doesn't take much to seat on someone else's desk, especially if it's in office space divided by cubicles. He boots up the PC from the TRK USB device.
- Step 2. Select Windows Password Resetting
- Step 3. Select your preferred option, I usually select Interactive winpass because it gives me the option to list user accounts, see their group membership, and status.
- Step 4. So if you select the interactive option, the file systems will be mounted and the registry loaded. Unless you have a multi boot system hit enter, otherwise select the right installation to mount
- Step 5. Select option 1 – Edit user data and passwords - user account status, from there you have the option to enter the user account which you’d like to modify, enter either the RID or the user account exactly as you see is displayed.
- Step 6. Select the user account to modify, either by typing 0x<RID> (the RDI for the user name, listed on the first column) or the user name exactly as it’s displayed.
- Step 7. In the user's property windows select the option to Clear or Edit the password. Reset or Edit password as you wish.
- Step 8. Quit Menu, reboot pc and log in as Alice.
Bob logged in as Alice, took the data he was looking for and soon he'll be out of the office. Yes, this is a very loud way of accessing someone else's computer, especially when the password is reset but in a regular office environment users forget their passwords all the time, it's not uncommon for a user to take fault for when their passwords don't work, even in situations when it had been reset by someone else.
Two weeks went by and Bob still working in the company, now that he got a hold of TRK he feels a sense of power which pushes him to do more. This time Bob doesn't want to reset the password, users questions too much how come their passwords changed overnight, besides the copying the data from Alice's PC to his USB proved to be more difficult than expected for him because he didn't have enough space on his thumb drive, now Bob wants to access everything on Anna's PC
Scenario 2. Create an open share with TRK. Gain access to someone else's data over the network
Background:
You need to have physical access to the "victim" PC
You should be able to boot up from an external source such a USB, CD, or network.
You have TRK ready
Workgroup network configuration
DHCP network
DHCP network
Here's what Bob does with TRK
- Step1. Connects TRK USB to Anna's pc, turns the computer on and Selects the boot option to boot from USB
- Step 2. PC boots up into TRK
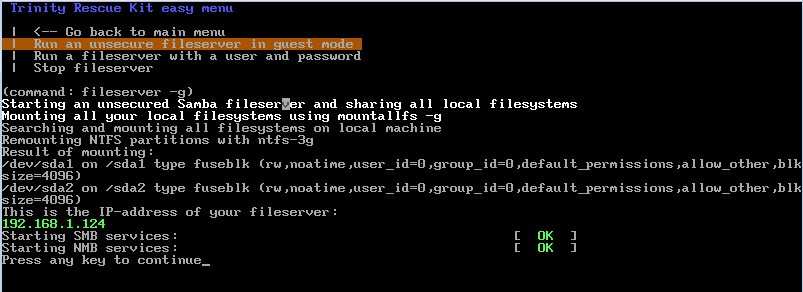
- Step 3. Selects Run a windows fileserver option
- Step 4. Selects Run an unsecure fileserver in guest mode option
TRK mounts the local partitions, loads the SMB and shares them in the network. The fileserver is published using the Anna's IP address. (quick note: if you are in a DHCP environment TRK will request an IP address from the DHCP server. IP settings can also be manually configured by suing the setip eth0 command from the TRK shell)
- Step 5. Uses Windows UNC to connect to Anna's new Shared drives over the network (Bob's is happy man now)
- Step 6. He gets the price: access to Anna's files. He just browses using explorer to copy what he wants.
- Step 7. After copying the data, Bob stops the file server and exists TRK. No visible traces, no drama, didn't take him long, ready to leave his company with a lot of data he wasn't supposed to get access to.
OK, Bob was successful in his two attempt but who cares, let's go over a couple of security best practices in the Layered Security approach.
- 1. Physical Control: Prevent physical access (though not possible in every situation it's something to consider)
- 2. Physical Control: Surveillance system, it serves as a deterrent.
- 3. Technical Control: Password protect system BIOS settings, this will prevent users from accessing-changing boot settings.
- 4. Technical Control: Enable Boot Security settings. Available in many BIOSes to prevent computers from booting to "unauthorized" OS.
- 5. Technical Control: Disable external devices such as CD, USB, and other ports.
- 6. Cryptography: Encrypting either data or full disk would rendered data unreadable.
- 7. Technical Control: Centralized administration, workgroup networks don't offer centralized management, log tracking,
- 8.Technical Control: Network Security, port security, vlan, ipsec.
Now that Bob has conquered Alice and Anna's documents he wants to go for the ultimate price before he walks out on them. He wants to have access to the HR manager's PC. That's right..., he's done it twice and he can do it again without getting caught and he's going after the big fish now.
This time he doesn't want access to some files or docs, he wants the whole computer. He knows that with TRK there's a much better option than stealing the HR manager's PC, he can make an exact copy over the network in less than it'd take for the manager to come back from lunch, he wants a clone..
It requires a little more of technical skills and work but Bob is determined.
Scenario 3. Cloning a PC over the network with TRK.
Background:
You need to have physical access to the "victim" PC
You should be able to boot up from an external source such a USB, CD, or network.
Two TRK boot devices
Workgroup network configuration
DHCP network
A computer similar computer as the HR manager's PC.
A laptop loaded with Virtual Box
In this case Bob is going getting a little bit more techie, after all he doesn't want to carry a tower computer to the office to commit his mischievous act. Instead of finding a computer with similar hardware to the HR Manger's one he has decided to clone to a virtual machine instead, that way he can bring his laptop loaded with Virtual Box and image to it, all thing still using TRK.
To accomplish his objective Bob does:
1. Install Virtual Box and create a new Virtual Machine
The name and the OS type settings are irrelevant for this purpose
Add the amount of memory allocated for the virtual machine, 1024 MB would suffice for the intended purpose.
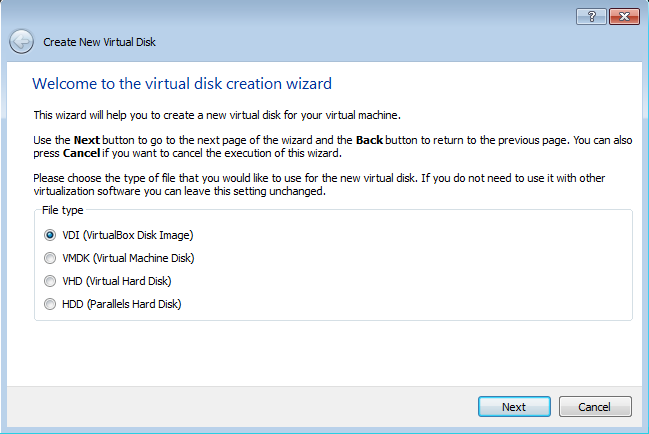
Create Virtual Disk
Select VDI type
Select fixed size for the storage details, this is very important! for our purpose TRK needs to see a "full disk" to image to otherwise the cloning will fail during transfer.
Leave the default location and enter the amount of hard disk space ( from the laptop hd) that will be allocated for the VM, the space must be the same or more than the physical computer being cloned. - Yes, our friend Bob has a 1 TR drive on his laptop so he should be fine-.
Create the VDI drive, the system will take the allocated space and create the drive, the process might take some time depending on the size and type of drive. In Bob's case he took care of the preliminary Virtual Box configuration before he came to the office.
The process is fairly fast over a 100 mpbs network and even faster is all hardware involved support the 1gbps.
After pc has been imaged, Bob can quit TRK, restart computers and life goes back to normal. He might have one more task to do though, even though he cloned the Manager's PC he still need to brake the password to get to be able to log in. It's not a big deal because he already did with Alice's computer.
Now, let's look at it from the administrative point of view. Besides the controls I mentioned earlier the most troubling lack of control i've seen in situations like this is the lack of proactive administration, or centralized administration. An unmanageable network is an insecure network, when the network is just a few people the office environment might be able to get away with a lot of the most stringiest controls but once the office has matured in its business practices the need for centralized administration and management is paramount. Let me clear, centralized administration, such as Windows Active Directory, Centralized AV, IPS-IDS, are not a silver bullet against attacks like this but it provides the necessary tools for someone with the technical knowledge to apply the appropriate controls to avoid situations like the ones described.
I usually refer to the NIST and NSA documents framework, I also use PCI and HIPAA standard whether the business requires to comply or not with such standards. The point is to be proactive when it comes to network security and adapt the frameworks and best practices to each business need.
Lastly, there are commercial solutions to protect each layer in the network, each company and administrator have their own preferences based on experience, price, corporate policies, etc. I have found McAfee to a solid company in the security realm, i have deployed and administered many McAfee solutions for clients and they have proven to be effective.
Visit our sites at www.precisetek.com and www.traversenet.us for technical and security services in NYC & NJ
DHCP network
A computer similar computer as the HR manager's PC.
A laptop loaded with Virtual Box
In this case Bob is going getting a little bit more techie, after all he doesn't want to carry a tower computer to the office to commit his mischievous act. Instead of finding a computer with similar hardware to the HR Manger's one he has decided to clone to a virtual machine instead, that way he can bring his laptop loaded with Virtual Box and image to it, all thing still using TRK.
To accomplish his objective Bob does:
1. Install Virtual Box and create a new Virtual Machine
The name and the OS type settings are irrelevant for this purpose
Add the amount of memory allocated for the virtual machine, 1024 MB would suffice for the intended purpose.
Create Virtual Disk
Select VDI type
Select fixed size for the storage details, this is very important! for our purpose TRK needs to see a "full disk" to image to otherwise the cloning will fail during transfer.
Leave the default location and enter the amount of hard disk space ( from the laptop hd) that will be allocated for the VM, the space must be the same or more than the physical computer being cloned. - Yes, our friend Bob has a 1 TR drive on his laptop so he should be fine-.
Create the VDI drive, the system will take the allocated space and create the drive, the process might take some time depending on the size and type of drive. In Bob's case he took care of the preliminary Virtual Box configuration before he came to the office.
Now that the "recipient" virtual computer has been successfully setup is time to move on to the actual act, Bob is ready to clone the HR Manager's PC to a virtual machine running on his laptop.
- 1. Boot up the HR Manager's PC from a TRK USB drive.
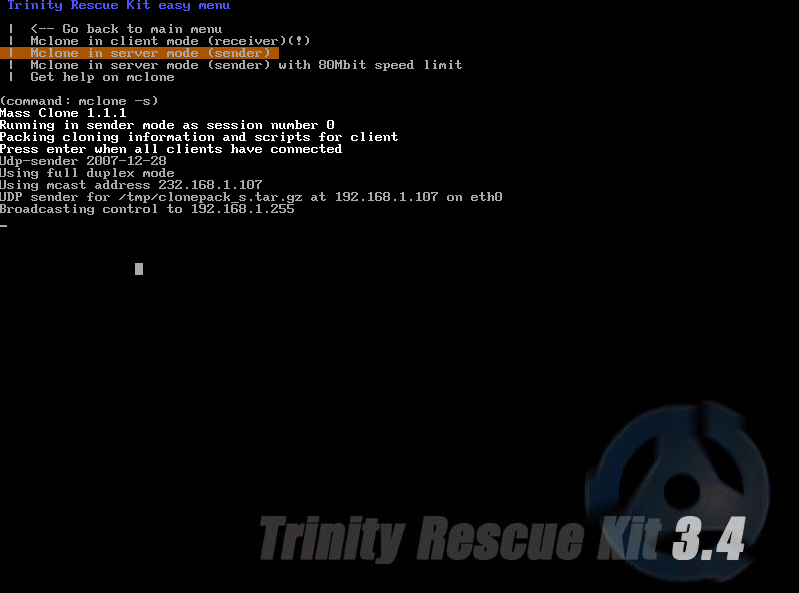
- 2. Boot up the Manager's PC and his VM with TRK, the boot up process is the same, what's going to change is the menu selection. Select Mclone: computer replication over the network.
- 3. On the Manager's PC Bob selects Mclone in server mode (sender)
- 4. Notice that TRK enables Mclone to broadcast to client computers in the same network segment, it can broadcast to one or multiple computers at a time. At this time the system is waiting for a client connection.
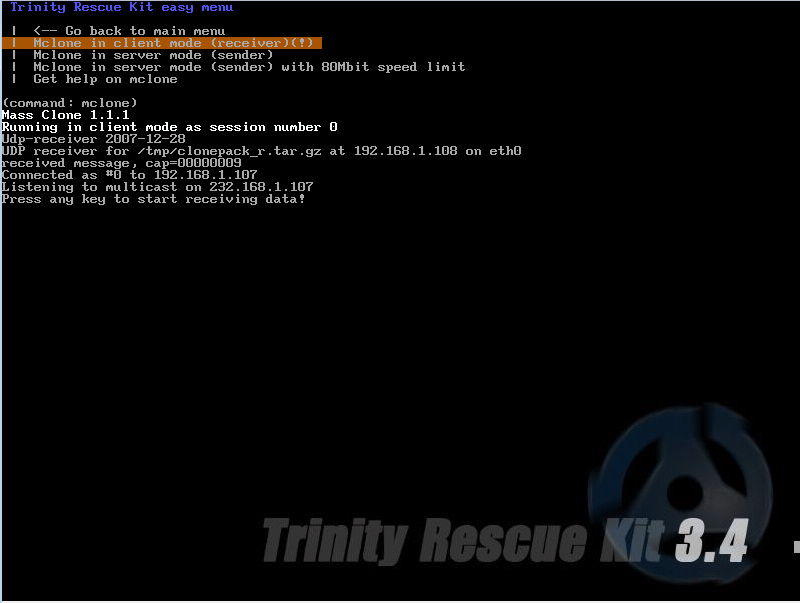
- 5. On his VM Bob selects Mclone in client mode (receiver) option.
- 6. Notice that system is ready to receive data from the sender, press any key to continue and watch magic happen...
- 7. Press any key an let the data transfer begin.
The process is fairly fast over a 100 mpbs network and even faster is all hardware involved support the 1gbps.
After pc has been imaged, Bob can quit TRK, restart computers and life goes back to normal. He might have one more task to do though, even though he cloned the Manager's PC he still need to brake the password to get to be able to log in. It's not a big deal because he already did with Alice's computer.
Now, let's look at it from the administrative point of view. Besides the controls I mentioned earlier the most troubling lack of control i've seen in situations like this is the lack of proactive administration, or centralized administration. An unmanageable network is an insecure network, when the network is just a few people the office environment might be able to get away with a lot of the most stringiest controls but once the office has matured in its business practices the need for centralized administration and management is paramount. Let me clear, centralized administration, such as Windows Active Directory, Centralized AV, IPS-IDS, are not a silver bullet against attacks like this but it provides the necessary tools for someone with the technical knowledge to apply the appropriate controls to avoid situations like the ones described.
I usually refer to the NIST and NSA documents framework, I also use PCI and HIPAA standard whether the business requires to comply or not with such standards. The point is to be proactive when it comes to network security and adapt the frameworks and best practices to each business need.
Lastly, there are commercial solutions to protect each layer in the network, each company and administrator have their own preferences based on experience, price, corporate policies, etc. I have found McAfee to a solid company in the security realm, i have deployed and administered many McAfee solutions for clients and they have proven to be effective.
Visit our sites at www.precisetek.com and www.traversenet.us for technical and security services in NYC & NJ